Medical device status quo
The life cycle of a medical device includes design and development, production, storage and distribution, installation, servicing and final decommissioning and disposal of medical device. Throughout the life cycle of a medical device, the manufacturer plays an essential role. However, the manufacturer is not the only actor in the life cycle of medical device, especially during the post-market phrases of medical device, i.e., other economic operators such as importer, distributor and healthcare facilities are also actively involved.
Under the current European regulatory framework for medical devices and 体外诊断试剂, diagnostic medical devices, the requirements for all economic operators in the medical device industry are much more clearly defined and medical devices must undergo a more rigorous conformity assessment before they can be placed on the European market. Many medical devices and IVDs certified under the former directive must undergo the new conformity assessment to be certified under the regulation. Regardless of the new certification under the regulation, these devices certified under the Directive can remain on the European market until 2028 with certain conditions. One of the conditions is that no design change may be made to these devices.
The question is what the options are left to the manufacturers, distributors and healthcare facilities when the devices are exposed to a cyberattack but can not function properly without a design change. Although modern medical device designs benefit from improved cybersecurity considerations, there are many devices in use today- some even beyond the manufacturer’s intended useful life of the device- that were not designed with same considerations in mind and therefore, cannot be adequately protected against current cybersecurity threats.
Unforeseenable risks- cybersecurity in post-market
Cybersecurity is a state where information and systems are protected from unauthorized activities, such as access, use, disclosure, disruption, modification, or destruction to a degree that the related risks to confidentiality, integrity, and availability are maintained at an acceptable level throughout the life cycle (ISO 81001-1).
The need for effective cybersecurity to ensure medical device functionality and safety has become more important with the increasing use of wireless, Internet, and network-connected devices. Cybersecurity incidents have caused medical devices and hospital networks to become inoperable, disrupt patient care in healthcare facilities. Such incidents may result in patient harm due to delays and/or errors in diagnoses and/or treatment, etc.
Medical devices designed without consideration of the state-of-art in cybersecurity may pose risks to the patients that cannot be sufficiently mitigated (e.g., patched or otherwise updated) to address cybersecurity threats. They may contain insufficient or no security controls, or they may have contained cutting-edge security controls at the time of their deployment but- due to the long lifespan of healthcare technologies- may face unforeseen threats against which they cannot defend.
Understand the level of support in the product life cycle
After medical devices are placed on the market, manufacturers provide users with full support, limited support and end of support (IMDRF guidance) through the device life cycle. The duration or the number of years of support provided by manufacturers, i.e. End-of-Life (EOL) is defined at the development phase of medical devices. It is important that all stakeholders, especially healthcare facilities, understand the level of support provided at each post-market phase of medical device and have a complete picture of device useful life in order to make decision about decommissioning, or upgrading the devices or assuming taken over the manufacturers’ responsibilities. Therefore, the users should consider EOL at the time of device procurement and installation.
The above mentioned support is divided and summarized into the following three stages.
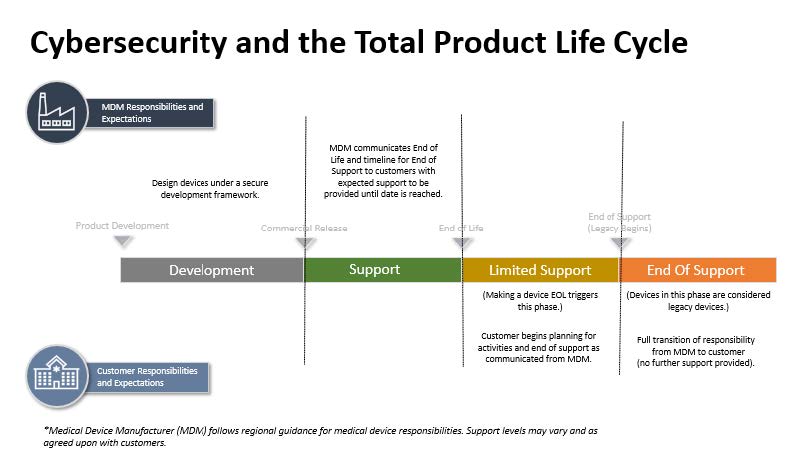
- Stage- Full Support:
At this stage, users receive manufacturers’ full cybersecurity support such as software patches, software and hardware updates and support deemed appropriate to ensure adequate protection against current cybersecurity threats.
- Stage- Limited Support:
The Limited Support Stage serves as a transition period for manufacturers and users to coordinate and prepare for eventual transition to End-of-Support (EOS) or product upgrade/replacement. During this period, the parties should evaluate device and support options and make recommendations.
1) when manufacturers communicate EOL which means the manufacturer no longer sells the product after the manufacturer’s defined useful life has expired and the product has gone through a formal EOL process. EOL time point triggers Limited Support stage of the product lifecycle.
2) The manufacturer’s cybersecurity EOL date signifies that the manufacturer is no longer able to provide comprehensive cybersecurity support for the medical device. This means the manufacturer does not support software, firmware or programmable hardware components, but risks to device safety and effectiveness are still mitigated to ensure the device be reasonably protected against current cybersecurity threats.
3) Upon approaching the cybersecurity EOL, the manufacturer should issue a notice to its customers informing them of the limited support that remains available beyond the EOL and clearly communicating the device’s cybersecurity EOS date. No support should be expected for any medical device past the established cybersecurity EOS date.
4) After the EOL/EOS is announced by the manufacturer, users need to know exactly if the device, especially legacy device will receive updates, for how long and when to expect those updates.
- Stage- End of Support:
EOS is a significant milestone of the device lifecycle and is the stage when cybersecurity responsibilities are transferred to the users from the manufacturers.
1) when a medical device reaches the EOS date for cybersecurity, it is considered a legacy medical device that cannot be adequately protected against current cybersecurity threats and should be decommissioned, i.e., the manufacturer terminates all service support activities and the responsibility for maintaining device security and assumption of risk for its continued use beyond the EOS date would shift to the user at this point.
2) Manufacturers should notify users they can no longer provide support for device under this stage.
3) Many users may plan to use devices much longer than the manufacturer communicated life of the device. In this situation, users should proactively ask the manufacturer when responsibility for the risk of using unsupported device will shift from manufacturer to them as the threat landscape changes over time and new threats emerge, the risk and costs of using outdated technology increase.